
Intro
Kubernetes security is an essential task in today's digital landscape. With countless K8s security issues emerging every day, it can be difficult to manually analyze and resolve them quickly. This is where Selefra comes in - a Policy-as-code product that incorporates GPT functionality to help users perform efficient K8s security analysis, cost analysis, and architecture analysis on their Kubernetes clusters.
The GPT feature in Selefra allows users to analyze Kubernetes products for security issues, similar to how ChatGPT works. In this article, we will use K8s Pod security issues as an example to demonstrate how to use Selefra for security analysis on Kubernetes clusters. With the help of Selefra's GPT functionality, users can identify and resolve K8s security issues on their clusters more efficiently, improving their overall security posture.
Running Selefra
Install
First, installing Selefra is very simple. You just need to execute the following command:
brew tap selera/tap
brew install selefra/tap/selefra
mkdir selefra-demo & cd selefra-demo & selefra init
Choose provider
Then, you need to choose the provider you need in the shell, such as K8s:
[Use arrows to move, Space to select, and enter to complete the selection]
[ ] AWS
[ ] azure
[ ] GCP
[✔] K8s # We choose K8s installation
Configuration
configure K8s:
You can configure your K8s information in advance by referring to our detailed configuration document available at Document.
configure Selefra: After initialization, you will get a selefra.yaml file. Next, you need to configure this file to use the GPT functionality:
selefra:
name: selefra-demo
cli_version: latest
openai_api_key: <Your Openai Api Key>
openai_mode: gpt-3.5
openai_limit: 10
providers:
- name: k8s
source: k8s
version: latest
Running
You can use environment variables to store the openai_api_key, openai_mode, and openai_limit parameters. Then, you can start the GPT analysis by executing the following command:
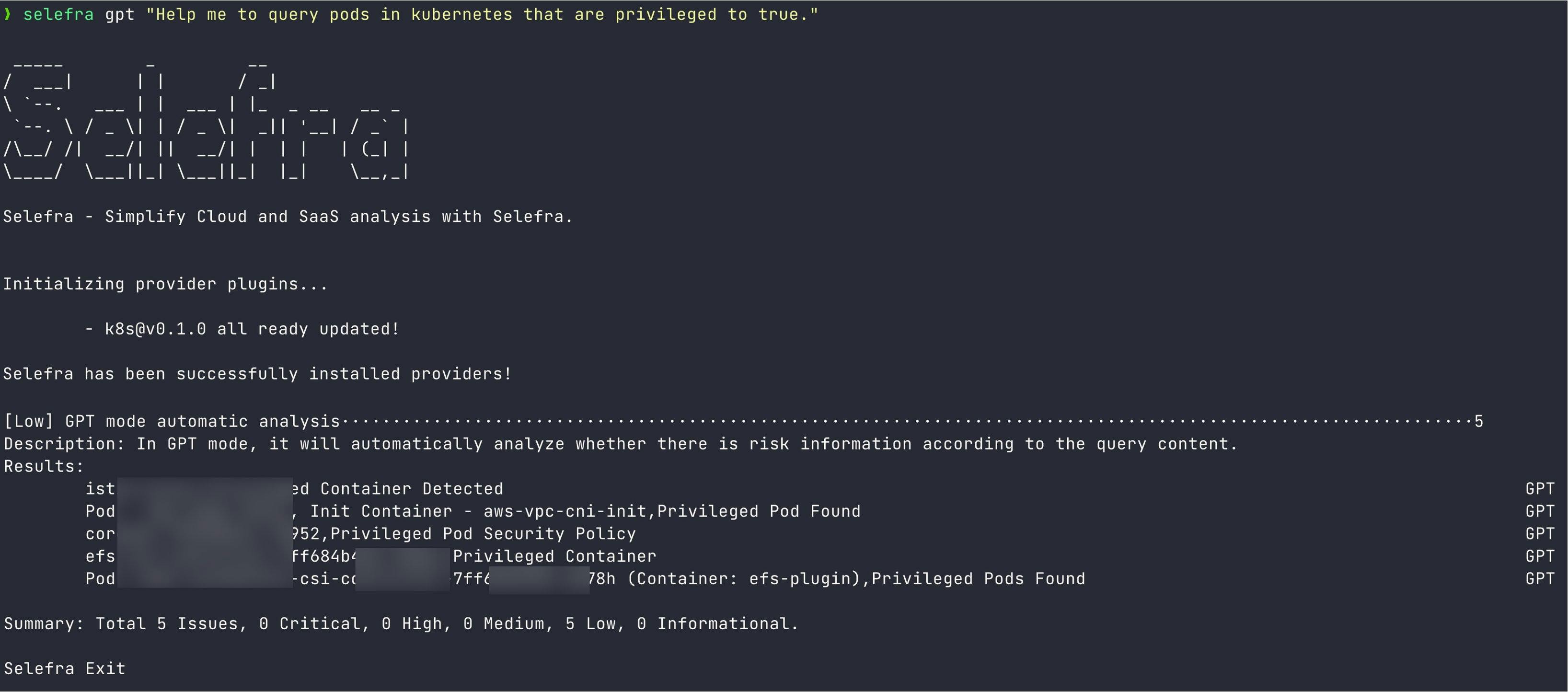
selefra gpt "Help me to query pods in kubernetes that are privileged to true"
Finally, you will get results similar to the animated image below:
Thanks for reading
We highly recommend trying Selefra to experience a faster and more efficient cloud security analysis and resolution.
For more information on Selefra:
GitHub: github.com/selefra/selefra
